The software has become a necessity in our daily lives, each activity now needs some kind of computational assistance and therefore Software Development.
The concept of Software Development and its use has come to stay in this century, and it will not stop in the coming future as well. The development process of software products is pretty complicated.
Therefore, to make it easy, it has been simplified by using different intelligent ways into systematic and detailed ways, step by step, which is known as the software development life cycle.
The software development life cycle includes all the small steps that are in the product management, design, and project management having all the steps, such as:
- Ideation & concept
- Wireframing & prototyping
- Technology selection
- MVP development
- Product development
- Quality assurance & testing
- Cloud & DevOps
- Launch and marketing
- Feedback analysis & improvement
This has the expected deliveries for a project, rules, and practices, and all the activities included for its completion. Engineer Master Solutions provide web and software solutions, software for startups, AI/ML, blockchain, and internet of things solutions.
In the whole path of software development, the Head puts their reliability on the development team with the written code and belief that the product will work properly.
This is a big deal because the authenticity of digital products is being questioned gravely across all industries, which could have serious consequences for companies with products based on possibly stolen codes.
In this article, we will talk about the need to safeguard the software codes and the utilization of Blockchain Technology in getting security.
Table of Contents
Why Do You Need To Secure Code?
In the times when there are fast launches of software development, the fast growth of digital solutions in the market, and the need for curators of these digital solutions to safeguard them against software threats. Following are the concerns:
- When your product’s codes are insecure, end-users (consumers) may see security alerts that discourage software downloads.
- Due to unauthorized use of code, the launched digital product (software solution) may be removed entirely.
- Experiencing a slew of legal blunders, as well as the time-consuming process of resolving them.
- Software vulnerability disclosure has a detrimental impact on both the product and the firm.
- For these product launches, codes are written on a regular basis, and proving ownership of these written codes is getting increasingly challenging.
Hire Dedicated Developer
Code Ownership
Startups, companies, product companies, and also small and big companies that have digital software products have to establish code ownership for the products that they launch in the digital market. If the companies are not able to do so, it has culminated in high-profile cases, and that too in billion dollars.
As a result, software outsourcing companies, in-house or offshore, are now putting in the extra effort to assign ownership of code and use various technological processes to secure code used in product development.
This implies that the software development can not replicate the code from anywhere else, they have to write it on their own., and prove its authenticity.
It is code theft when a software development company assigns ownership to a client of code they did not create, which can result in a lot of legal issues.
There are various factors that are considered in the code ownership journey:
- All transaction records are securely stored by the software programmers or remote developers you engage.
- Code signing differs from SSL in that the developers sign the codes to establish ownership.
- There should be a clear trail of dates and time stamps throughout the development process.
But, as we all are aware that there is constant development in the technological processes. Therefore, companies are adopting different ways to prove code ownership and one of them is the use of Blockchain Technology.
What Is Blockchain Technology?
Blockchain Technology is the technology that is established on the use of data structures, cryptographic, with integrity, consistency, autonomy, and built-in feature of security that takes care of the authenticity of transactions.
Digital currencies like bitcoin are built on the blockchain technology process. This decentralized system is being used by software development companies to prove the authenticity of codes, prove ownership, and ensure the security of digital products.
Blockchain technology stores data structure in blocks, which are linked in a cryptographic chain format that ensures security. In addition, the decentralized system process ensures all transactions within the block of data are validated only by a consensus of participants.
It is nearly impossible to penetrate and tamper with blockchain technologies because of their complexity.
Several fundamental principles underlie blockchain technology, which ensures the security of the network.
- Through the use of a decentralized system, no central servers are required. It is therefore impossible to compromise all servers and disrupt the network or alter existing data.
- Peer-to-peer (P2P) networks are used in transaction processes.
- Modern data encryption technology enables digital signatures that can be used by all parties to sign transactions.
- The cryptographic chain format secures individual data blocks on the network.
- Immutable records contain time stamps and dates, as well as the author’s details.
The use of blockchain technology in software security – blockchain security provides a comprehensive tamper-proof system based on cybersecurity frameworks and cryptography.
Securing Software Development Codes With Blockchain Technology
The principles of Blockchain Technology imply that the system has an unchangeable database. This means the use of Blockchain Technology in code safety can not be altered and you can prove your company’s ownership very easily.
You can also hire a blockchain developer to add Blockchain Technology to your Software Development Code while safeguarding it.
These are some tips for securing codes using Blockchain Technology:
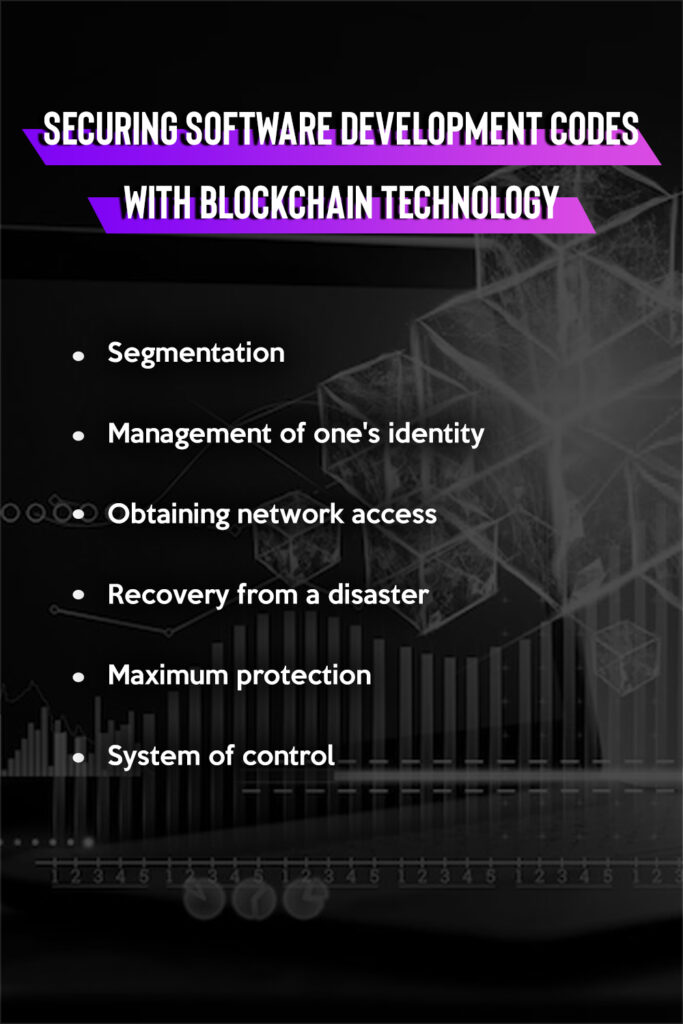
You can set up smart contracts with conditions allowing only authorized parties to utilize your code after successfully securing ownership of your codes as transactions on the blockchain.
Adopt Blockchain Technology Process In Securing Your Codes
The utilization of Blockchain technology in the Security of Code of Software Development is new but is highly beneficial. It is a very complex process, but with time it is evolving in various parts, to provide robust and reliable safety in all the industries.
Therefore, you might find a software development company with blockchain development solutions, like Engineer Master Solutions, to build by-products and safeguard your code ownership for all digital content.


 Like
Like LOVE
LOVE Win
Win Cute
Cute LOL
LOL OMG
OMG WTF
WTF Fail
Fail


